Introduction: Why Supply Chain Security Is the New Cloud Battlefield
Cloud security has evolved far beyond network firewalls, IAM policies, and endpoint monitoring. Today’s most critical security risks do not originate from exposed ports or misconfigured storage buckets. They originate from the software supply chain.
Table of Contents
Modern applications are assembled, not written from scratch. They depend on:
- Open source libraries
- Third party packages
- Container base images
- CI CD pipelines
- Infrastructure as Code templates
- Artifact repositories
- Cloud managed services
A typical microservices based enterprise application may contain thousands of indirect dependencies. Every dependency represents a potential attack surface.
This is where two powerful frameworks come into play:
- SALSA, Supply chain Levels for Software Artifacts
- SBOM, Software Bill of Materials
SALSA, originally introduced by Google and now governed by the Open Source Security Foundation, defines measurable levels of build system security.
SBOM, strongly advocated by agencies such as CISA, provides transparency into software composition.
Together, they form the foundation of secure cloud native software delivery.
This guide explores:
- Deep technical understanding of SALSA
- Full SBOM lifecycle integration
- Cloud native architecture implementation
- Enterprise examples
- DevSecOps alignment
- Governance and compliance impact
Section 1: The Modern Cloud Supply Chain Threat Landscape
The Evolution of Cloud Applications
Earlier enterprise applications were monolithic:
- Single runtime
- Few dependencies
- Manual deployments
- Limited automation
Today’s cloud architecture includes:
- Kubernetes clusters
- Container orchestration
- Auto scaling workloads
- Serverless functions
- CI CD automation
- Infrastructure as Code
- API driven integrations
This shift increased agility but also dramatically expanded the attack surface.
How Supply Chain Attacks Work
Attackers target upstream components instead of attacking production directly.
Common attack vectors:
- Dependency poisoning
Malicious code inserted into open source libraries. - Compromised CI pipelines
Build scripts modified to inject backdoors. - Tampered container images
Unauthorized artifact upload to registry. - Fake package repositories
Typosquatting attacks. - Compromised developer credentials
Malicious commit injection.
These attacks are difficult to detect using traditional runtime security tools.
Section 2: Deep Dive into SALSA
What SALSA Really Protects
SALSA is not a vulnerability scanner. It is not a code analysis tool.
SALSA protects the integrity of the software build pipeline.
It answers critical questions:
- Was this artifact built from verified source code?
- Was the build process tampered with?
- Can we cryptographically prove origin?
- Can anyone forge this build?
SALSA enforces strong build integrity guarantees.

SALSA Threat Model
SALSA protects against:
- Insider threats
- Compromised CI runners
- Malicious dependency injection
- Artifact forgery
- Build system manipulation
It does not directly prevent vulnerabilities in code. Instead, it ensures that what you built is what you intended to build.
SALSA Core Components
1. Source
Version controlled repository.
Access controlled.
Signed commits recommended.
2. Build System
Automated CI service.
Isolated execution.
Ephemeral environment.
3. Provenance
Cryptographically signed metadata that includes:
- Source commit hash
- Build timestamp
- Builder identity
- Dependency references
- Environment details
4. Artifact
The final output:
- Container image
- Binary
- JAR file
- Deployment package
SALSA Levels Explained in Enterprise Context
Level 1, Scripted Build
Minimum viable security.
- Build scripts exist
- Source control present
- Provenance generated
Still vulnerable to CI compromise.
Level 2, Hosted Build Service
Improved security.
- Managed CI platform
- Signed provenance
- Access control policies
Reduces manual manipulation risk.
Level 3, Hardened Build Environment
Enterprise recommended level.
- Isolated build containers
- No network access during build
- Authenticated dependencies
- Non falsifiable provenance
This prevents malicious injection during pipeline execution.
Level 4, Reproducible and Verifiable Builds
Highest assurance.
- Reproducible builds
- Two person review enforced
- Hermetic build environments
Primarily used in defense, financial systems, and critical infrastructure.
Section 3: Deep Dive into SBOM
What Is SBOM in Technical Terms
SBOM is structured metadata describing all components included in software.
Think of it as a dependency inventory with cryptographic references.
It includes:
- Direct dependencies
- Transitive dependencies
- Version numbers
- Licenses
- Hash values
- Supplier information
Why SBOM Is Critical in Cloud Security
Without SBOM:
- You do not know if you are affected by new CVEs.
- You cannot quickly respond to zero day vulnerabilities.
- You cannot ensure license compliance.
- You lack supply chain transparency.
With SBOM:
- Vulnerability impact analysis becomes immediate.
- Automated policy enforcement becomes possible.
- Risk assessment becomes measurable.
SBOM Formats
Common formats include:
- SPDX
- CycloneDX
Both are machine readable and integrate with security scanners.
Section 4: How SALSA and SBOM Work Together
SALSA ensures build integrity.
SBOM ensures dependency transparency.
Example Analogy
SALSA answers:
Was this cake baked in a trusted kitchen?
SBOM answers:
What ingredients are inside this cake?
Both are required for full confidence.
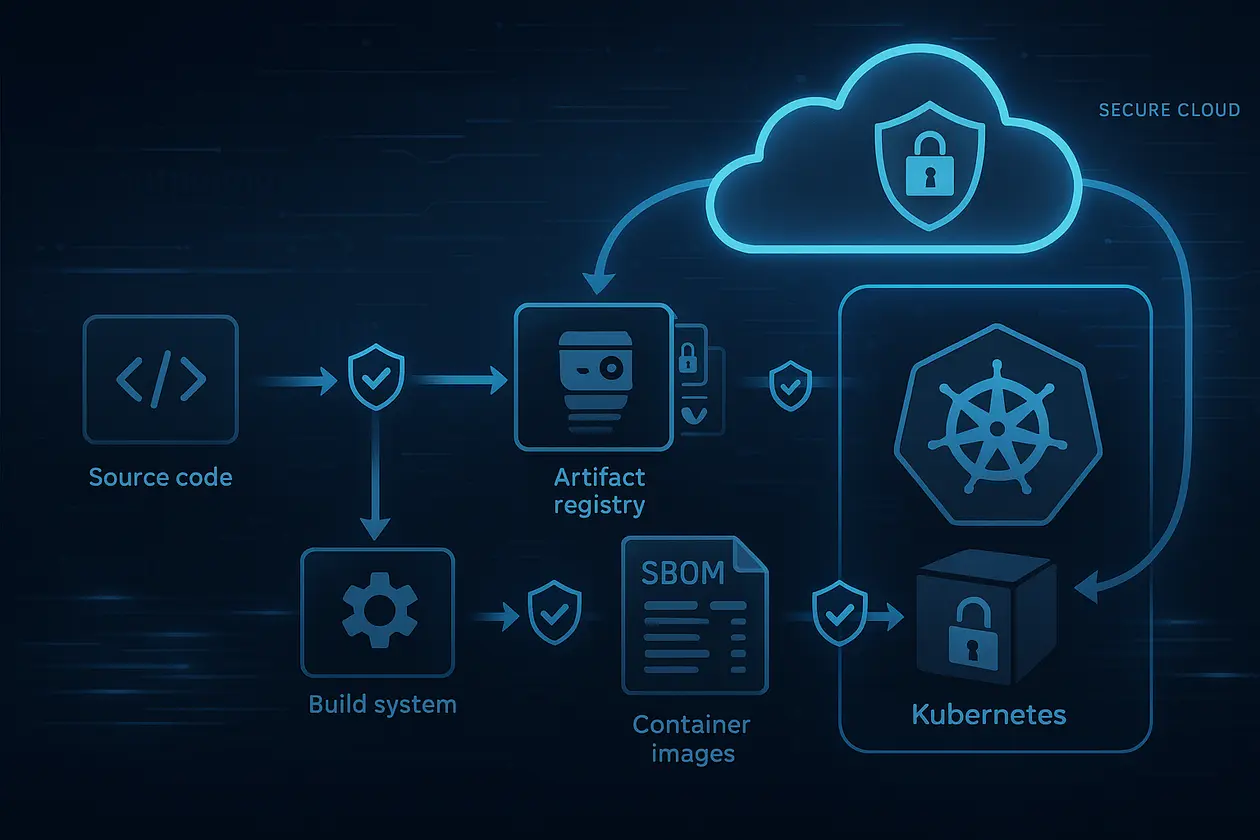
Section 5: Enterprise Cloud Implementation Example
Let us design a real world architecture for a financial technology company deploying on Kubernetes in a multi cloud environment.
Step 1: Source Control Hardening
- Git repository with signed commits
- Branch protection rules
- Mandatory peer review
Step 2: Hardened CI Pipeline
- Ephemeral runners
- No shared credentials
- No persistent workspace
- Restricted outbound network
Step 3: SBOM Generation During Build
During CI execution:
- Dependency tree analyzed
- SBOM generated automatically
- SBOM stored as artifact
Step 4: Provenance Generation
Build system produces:
- Signed provenance file
- Attestation metadata
- Builder identity signature
Step 5: Secure Artifact Registry
Container image stored with:
- SBOM attached
- Provenance attached
- Signature enforced
Step 6: Kubernetes Admission Controller
Before deployment:
- Validate artifact signature
- Validate provenance
- Verify SBOM vulnerability status
If verification fails, deployment is blocked.
Step 7: Runtime Monitoring
After deployment:
- Monitor runtime anomalies
- Detect drift
- Compare running image hash with original provenance
Section 6: Cloud Native Architecture with SALSA and SBOM
A secure architecture includes:
- Identity and Access Management integration
- Secure CI CD pipeline
- Artifact signing
- SBOM registry
- Policy as Code engine
- Container runtime protection
This transforms your cloud into a zero trust software execution environment.
Section 7: Governance and Compliance Impact
Regulated industries require:
- Traceability
- Audit trails
- Software origin proof
- Dependency transparency
SALSA and SBOM provide audit ready evidence.
This is especially critical for:
- Financial services
- Healthcare platforms
- Government contractors
- SaaS providers
Section 8: Challenges in Enterprise Adoption
Implementation requires:
- Cultural shift toward DevSecOps
- Pipeline redesign
- Toolchain integration
- Developer training
- Executive sponsorship
Organizations often fail when they treat supply chain security as an afterthought.
Section 9: Strategic Roadmap for Enterprises
Phase 1, Visibility
Generate SBOM for every build.
Phase 2, Integrity
Implement provenance signing.
Phase 3, Enforcement
Block unsigned artifacts.
Phase 4, Continuous Assurance
Automate verification at runtime.
Section 10: The Future of Cloud Supply Chain Security
Expect:
- Mandatory SBOM submission in procurement
- Automated cross cloud trust verification
- AI based anomaly detection in build pipelines
- Policy driven artifact federation
Supply chain security will become a board level KPI.
Final Conclusion
Cloud security must evolve beyond infrastructure defense.
The future belongs to organizations that can:
- Prove software origin
- Verify build integrity
- Track every dependency
- Enforce cryptographic trust
SALSA and SBOM are not optional frameworks.
They are foundational pillars of secure cloud native engineering.
For technology leaders, architects, DevSecOps engineers, and cloud strategists, mastering these frameworks defines the next generation of secure digital transformation.